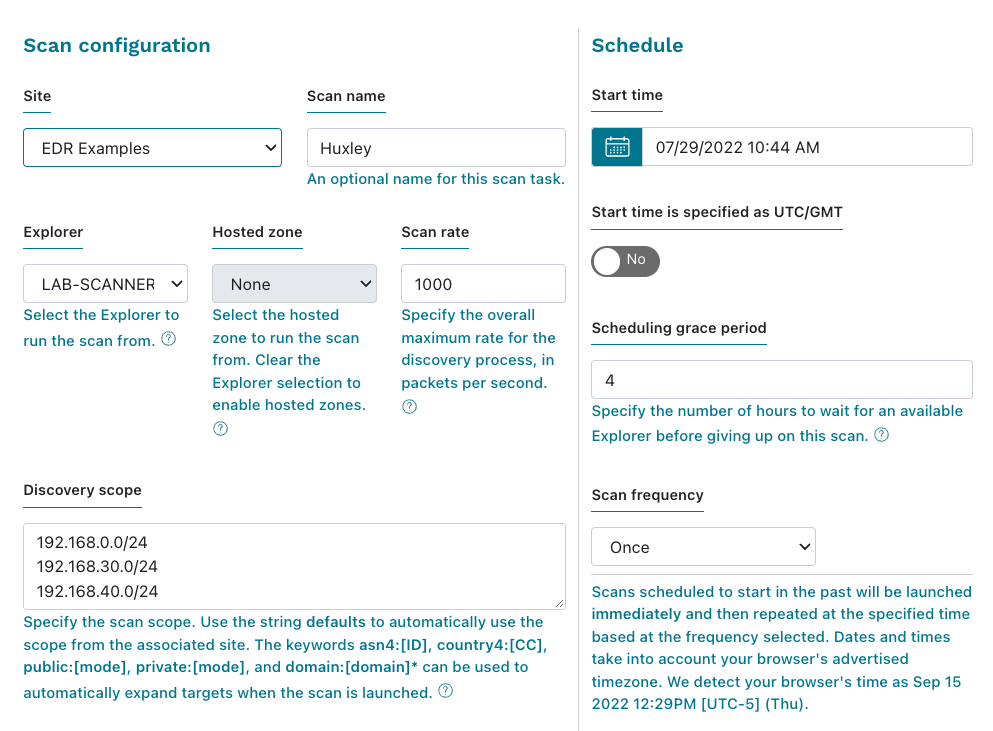
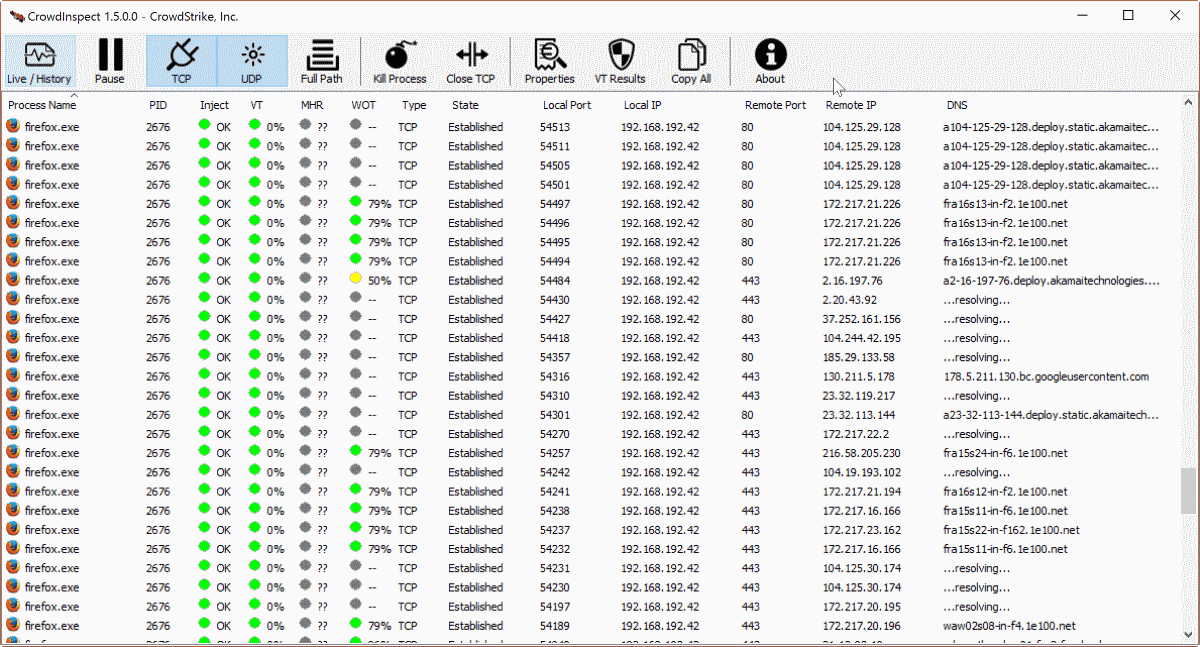
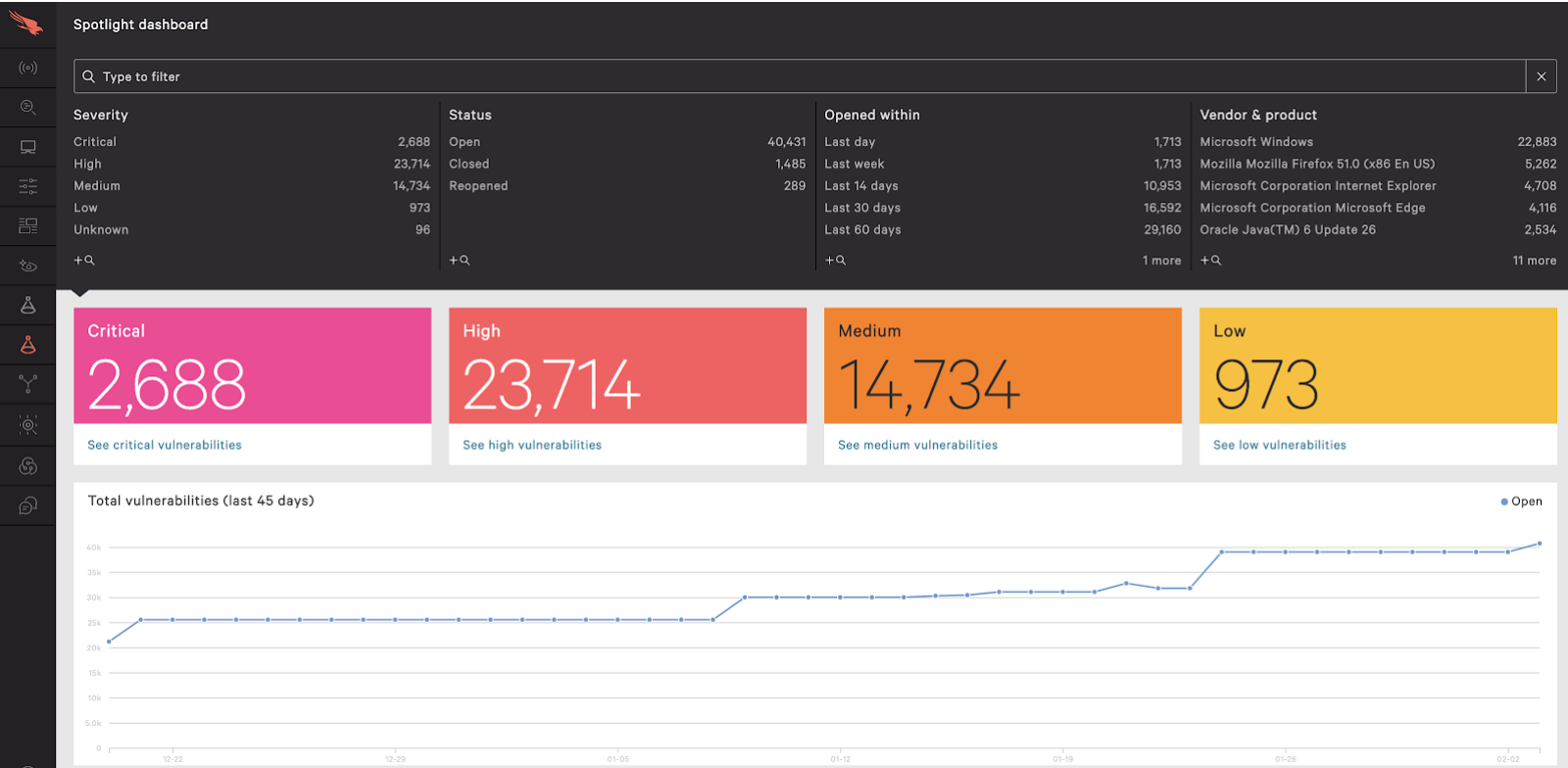
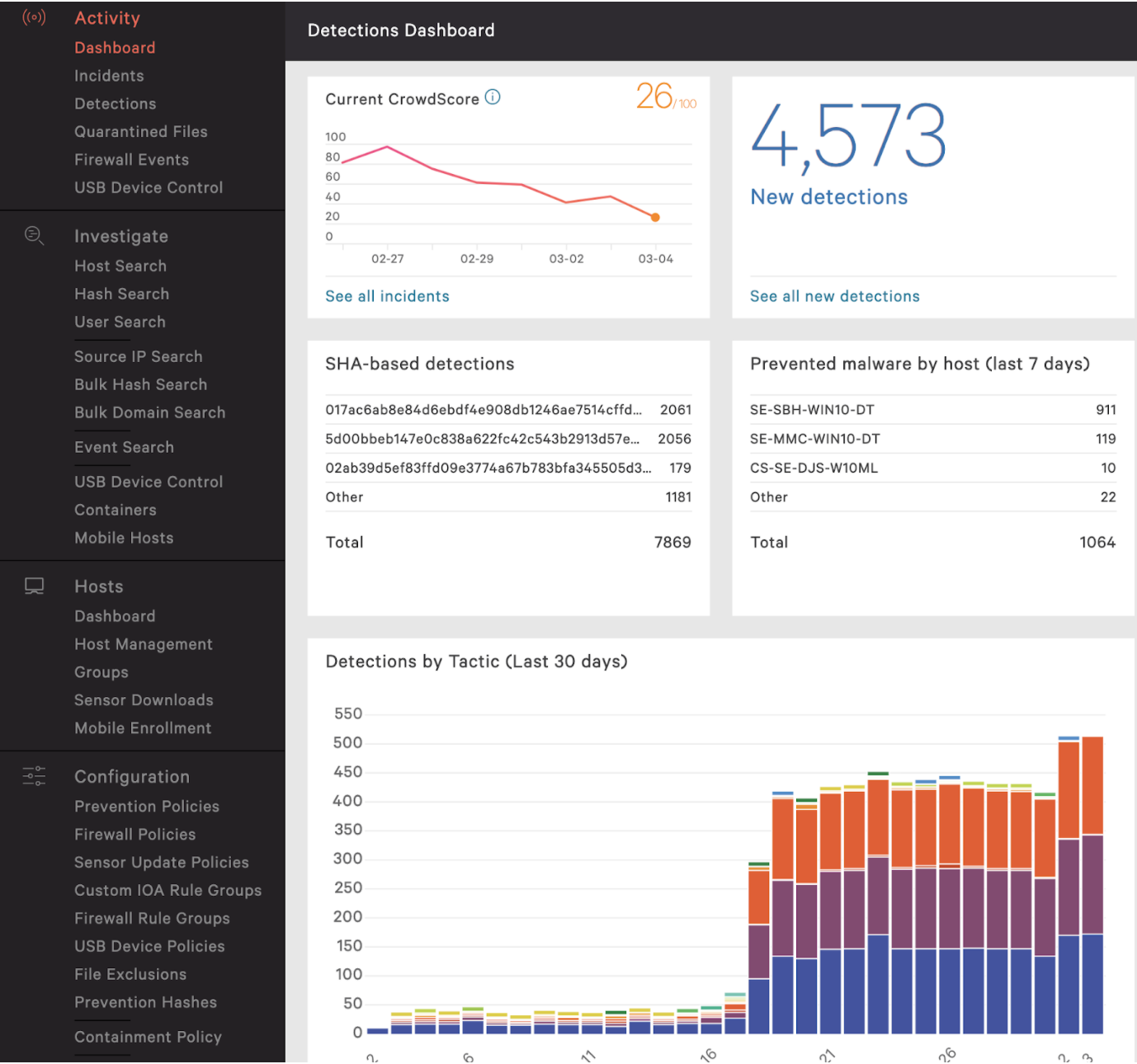
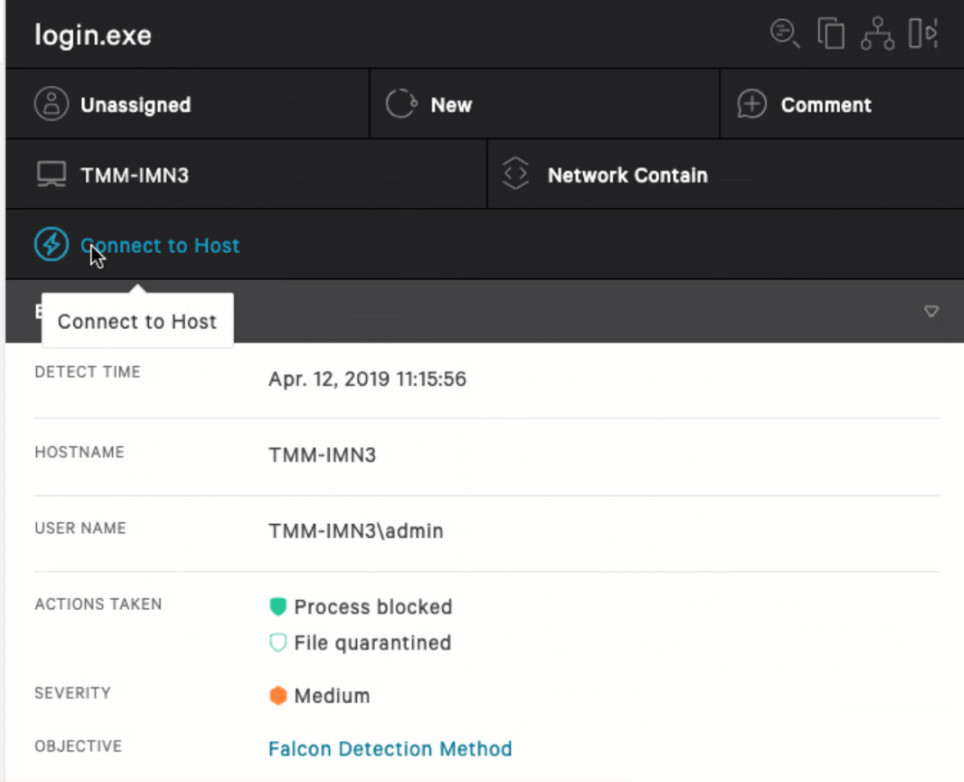
How to Run an On-Demand Scan with CrowdStrike - Knowledgebase / Security / CrowdStrike - SOU IT and Service Center Help Desk

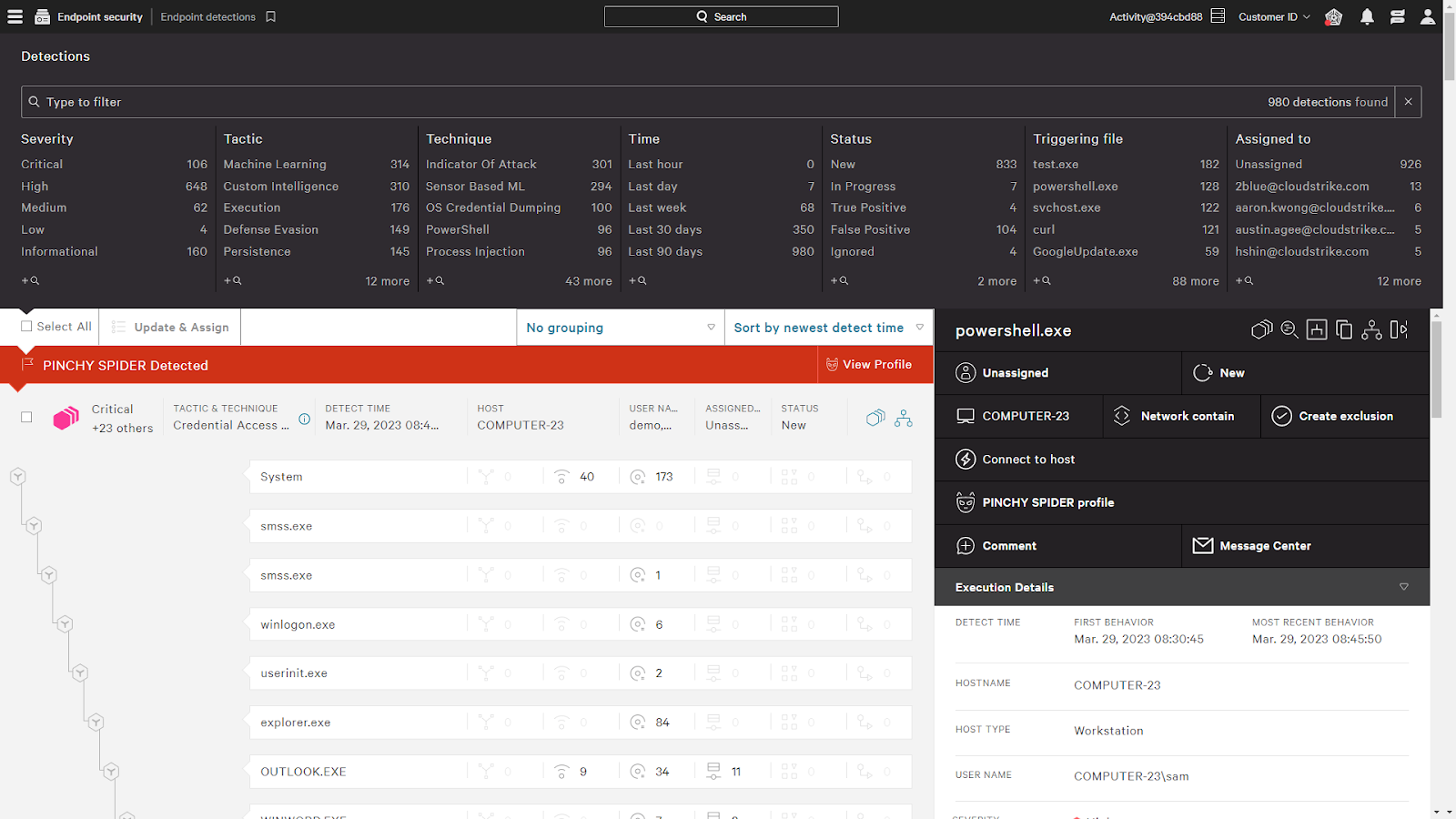
Renseignements sur les attaquants et failles exposées sur Internet : CrowdStrike dote son faucon d'un troisième œil pointé vers l'extérieur
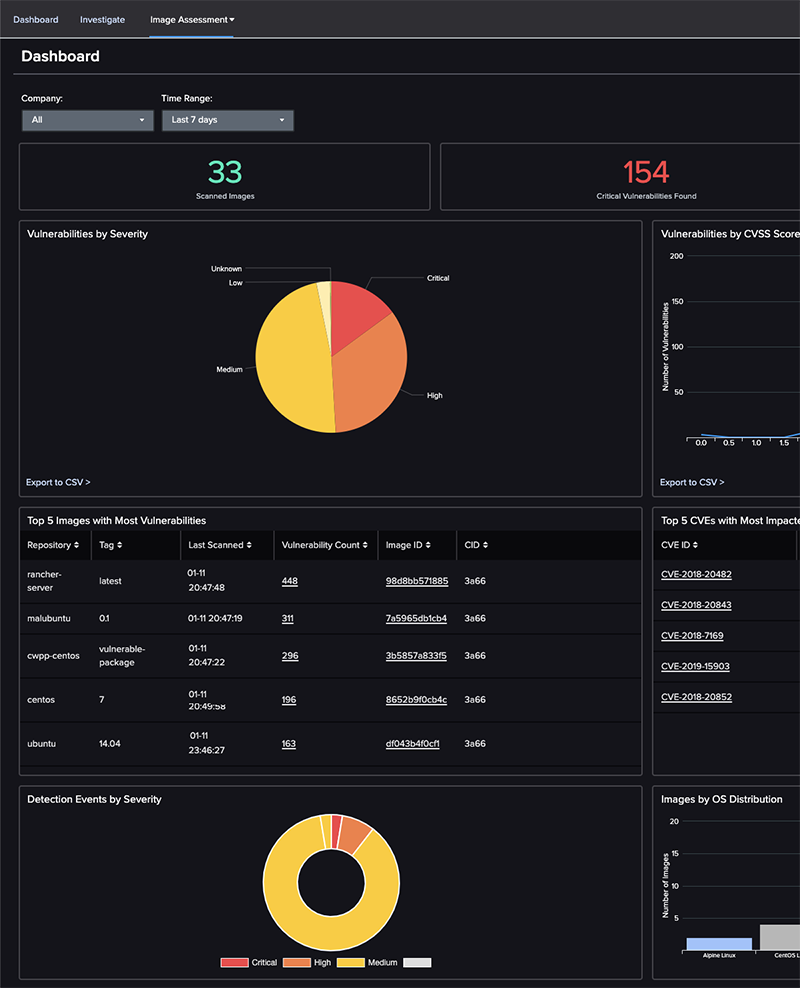
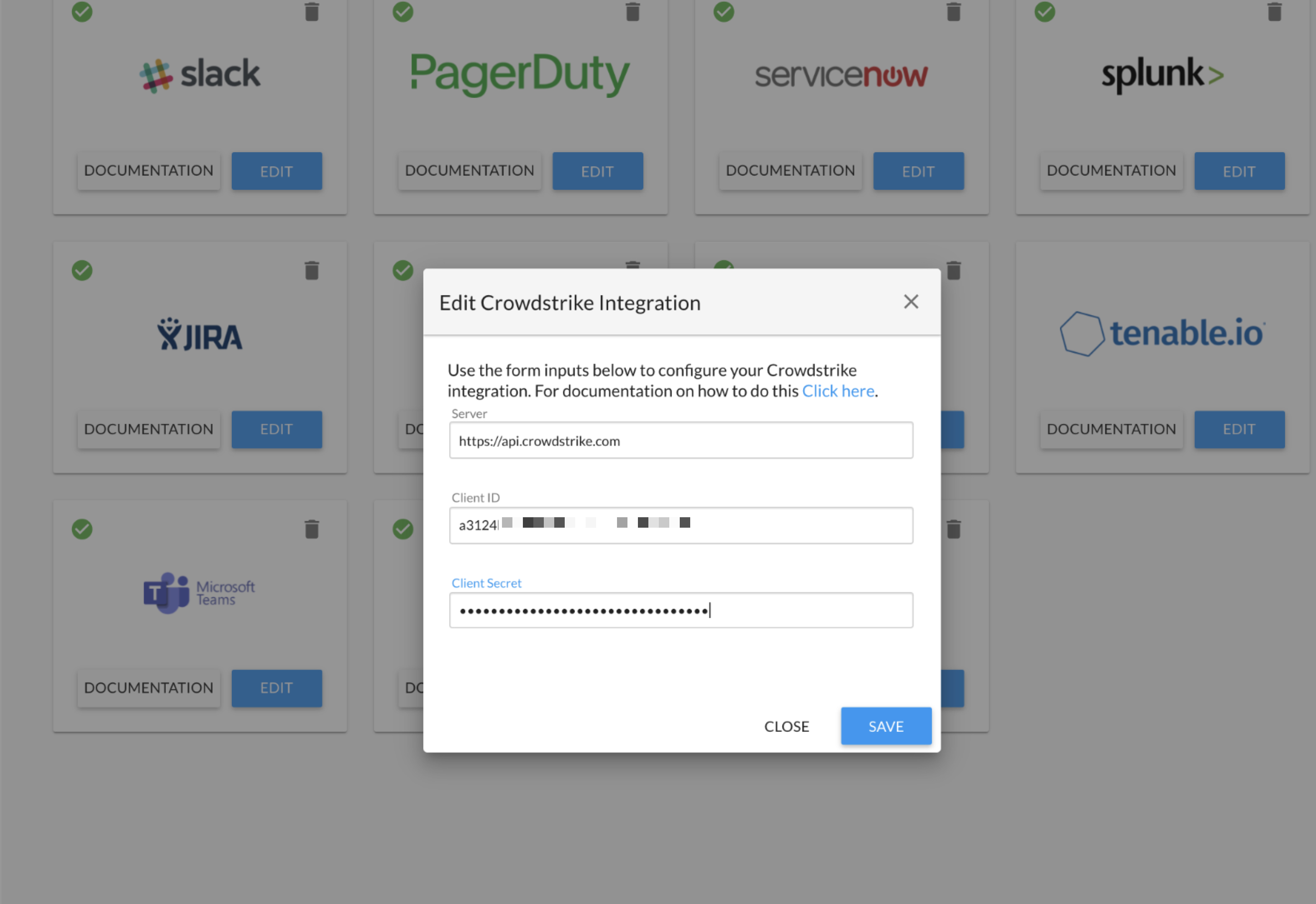
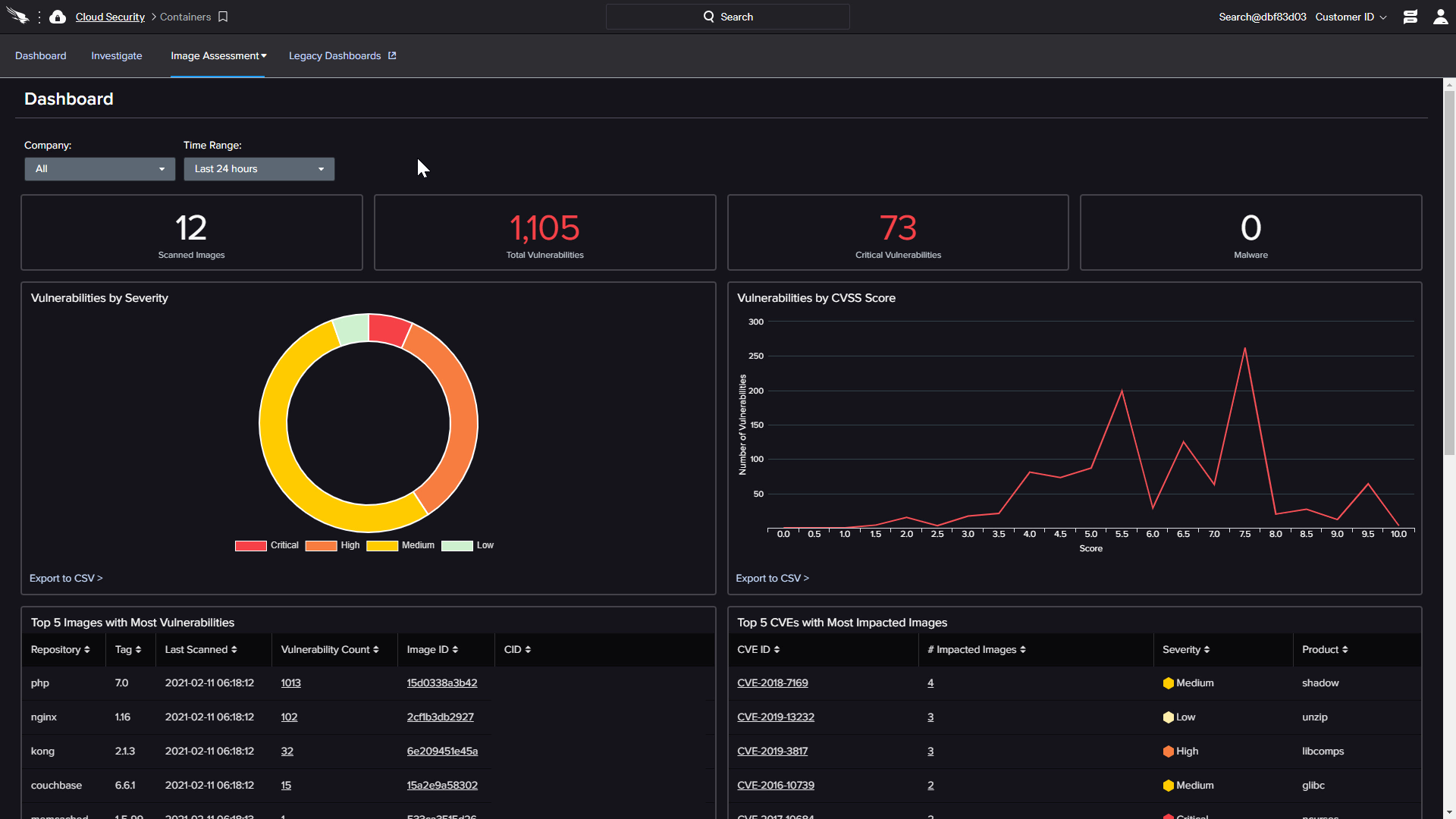
GitHub - CrowdStrike/container-image-scan: Code to scan a container with CrowdStrike and return response codes indicating pass/fail status.